"Conficker/Downadup" worm that infected millions of PCs worldwide in the past month – though past results suggest it might have limited success.
The reward – for information leading to the capture and conviction of the author or authors of the software – follows similar cash incentives offered by Microsoft to catch virus writers since 2003.
"The Conficker worm is a criminal attack. People who write this malware have to be held accountable," said George Stathakopoulos, of Microsoft's Trustworthy Computing Group. "Our message is very clear – whoever wrote this caused significant pain to our customers and we are sending a message that we will do everything we can to help with your arrest."
Graham Cluley, of the antivirus company Sophos, said: "Offering substantial rewards can do no harm. If a culprit isn't found then Microsoft hasn't lost anything, and it may just entice some members of the computer underground to come forward with information. People considering releasing malware in the future should take careful note of this and think again."
Microsoft has brought together a wide group from within the industry to combat the effects of Conficker, which attempts to connect to a randomly generated list of internet domains every day. Experts fear that one of those domains will be a "control" site that will instruct the infected machines to perform an as-yet-unkown harmful action.
"The best way to defeat potential botnets like Conficker/Downadup is by the security and domain name system communities working together," said Greg Rattray, the chief internet security advisor at the Internet Corporation for Assigned Names and Numbers, in a statement: "ICANN represents a community that's all about co-ordinating those kinds of efforts to keep the internet globally secure and stable."
But while the words – and amounts on offer – are dramatic, it is hard to know whether they will be effective. Microsoft set up a $5m fund to catch virus writers in November 2003, shortly after another worm dubbed "Blaster" infected millions of computers and disrupted communications for thousands of companies. It offered $250,000 for the writer of that worm, and for a number of other viruses, such as Zotob, Sobig and Sasser. Though the alleged authors of Zotob and Sasser were caught, it has never been made clear whether the bounties were paid out.
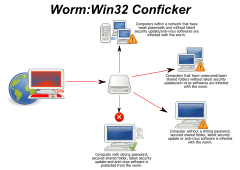
The Conficker worm though has caused far more damage than the amount being offered as a bounty. It has infected millions of PCs worldwide, including parts of the French navy and air force and the American air force. Security experts are still trying to work out what its intent is, although they note that it spreads throughout any network to which a Conficker-infected machine is connected.
That could mean it is either intended to create a "botnet" of machines that could be used to send spam, or a network that would send private information such as credit card numbers and passwords to an unknown location on the net.
Although Microsoft released a "patch" in October for its software that should have prevented computers being infected, many companies and organisations did not install it because they were worried about disrupting their existing setup. A version of Conficker began circulating at the same time as Microsoft released its patch, but had little effect.
The lack of updating left a huge security hole which hackers abruptly exploited in mid-January when a new version of a "worm" that exploited the weakness appeared, apparently written by the same team that wrote the original.
The new worm attempts to crack the passwords of machines on a network using the computing power of the infected machine to apply a "brute force" approach – so that passwords such as "admin", "password" or "123456" on potential target machines will quickly be broken.
Once it has infected a machine, the software also tries to connect to up to 250 different domains with random names every day. Researchers believe that one of them will be the intended "control" domain, and that when the computers connect to it they will download a fresh program that will take over the infected computer.
reff. Charles Arthur, guardian.co.uk
Conficker detail's
from Wikipedia
 | |
| Common name | Conficker |
|---|---|
| Aliases |
|
| Classification | Unknown |
| Type | Computer worm |
| Subtype | Computer virus |
Conficker, also known as Downup, Downadup and Kido, is a computer worm targeting the Microsoft Windows operating system that was first detected in October 2008.An early variant of the worm propagated through the Internet by exploiting a vulnerability in the network stack of Windows 2000, Windows XP, Windows Vista, Windows Server 2003, Windows Server 2008, Windows 7 Beta, and Windows Server 2008 R2 Beta that was discovered earlier that month.The worm has been unusually difficult for network operators and law enforcement to counter because of its combined use of advanced malware techniques.
Although the origin of the name "conficker" is not known with certainty, Internet specialists and others have speculated that it is a German portmanteau fusing the term "configure" with "ficken", the German word for "to fuck". Microsoft analyst Joshua Phillips describes "conficker" as a rearrangement of portions of the domain name "trafficconverter.biz".


No comments:
Post a Comment